Securing data in the age of algorithms
Algorithms have exponentially changed the way data is processed, analysed, and used. Personalised recommendations on streaming platforms to predictive analytics in healthcare, algorithms have become the backbone of modern innovation. However, this transformation comes with inherent risks, particularly to data security and privacy. As organizations increasingly depend on algorithms, the challenge lies in balancing innovation with the protection of sensitive information.
This article explores the evolving landscape of data security in the age of algorithms, highlighting key risks, regulatory implications, and strategies to mitigate these challenges. By understanding the intersection of algorithms and data security, businesses can harness the full potential of these technologies while safeguarding trust and compliance.
The algorithmic revolution and data explosion
Algorithms act as the engine behind the discovery of insights in gigantic amounts of data. Internet of Things devices, digital transformation initiatives, and cloud computing are the drivers for unprecedented data growth. In 2025, it is estimated that global data creation will reach 175 zettabytes annually. Algorithms, powered by advanced machine learning (ML) and artificial intelligence (AI), are critical in deriving actionable insights from this vast data pool. This exponential growth is fueled by:
1.IoT devices: Billions of connected devices continuously generate real-time data, from smart homes to industrial IoT in manufacturing and logistics.
2.Cloud computing: Cloud platforms facilitate seamless storage and processing of vast datasets, enabling rapid deployment of data-driven solutions.
3.Digital transformation: Organizations across industries are adopting digital tools and platforms, amplifying data generation and utilization.
These algorithms are able to process complex datasets at speeds and accuracies beyond human capacity, hence revolutionizing operations in such fields as:
While these applications demonstrate the transformative power of algorithms, the underlying dependence on sensitive data makes robust security measures imperative.
Risks Associated with Algorithmic Data Use
As organisations increasingly depend on algorithms, new risks emerge that can have an impact on the data, security, and privacy. Algorithmic dependency raises several threats, including:
These risks encompass various challenges. Addressing these concerns is crucial as algorithms become more integrated into business processes.
Regulatory Implications
Governments and regulatory bodies around the world are implementing stringent requirements to deal with data security and algorithmic accountability. Key regulations include:
1.General Data Protection Regulation (GDPR): Mandates data minimization, transparency, and accountability in algorithmic decision-making. Violations can lead to substantial fines.
2.Digital Personal Data Protection Act (DPDPA) 2023: India’s DPDPA focuses on protecting personal data and ensuring organizations implement robust security measures.
3.AI Act (European Union): Proposes risk-based categorization of AI systems, requiring high-risk systems to undergo rigorous testing and compliance checks.
4.California Consumer Privacy Act (CCPA): Grants consumers rights to access and control their data, impacting how algorithms utilize personal information.
Compliance with these regulations necessitates integrating security and privacy principles into the design and deployment of algorithms.
Best practices for securing data in algorithmic environments
Organisations must adopt a comprehensive approach to secure data in the age of algorithms. This includes technical, organizational, and ethical measures:
1. Data encryption: Encrypt data both at rest and in transit to prevent unauthorized access. Advanced encryption techniques, such as homomorphic encryption, enable computation on encrypted data without decryption.
2. Differential privacy: Incorporate noise into datasets to protect individual identities while maintaining the overall utility of the data.
3. Secure training environments: Ensure datasets used for training algorithms are sanitized and free from malicious inputs. Utilize secure multi-party computation (SMPC) to enable collaborative training without exposing raw data.
4. Explainability and transparency: Develop interpretable algorithms to enhance trust and detect anomalies. Frameworks like SHAP (SHapley Additive exPlanations) and LIME (Local Interpretable Model-agnostic Explanations) aid in making AI systems more transparent.
5. Robust authentication and access controls: Implement multi-factor authentication and role-based access controls to restrict unauthorized access to data and models.
6. Adversarial robustness: Design algorithms resilient to adversarial attacks by stress-testing models with adversarial examples during development.
7. Regular audits and monitoring: Conduct periodic audits of algorithms and data processing systems to identify vulnerabilities. Real-time monitoring tools can detect and respond to anomalies promptly.
8. Ethical AI governance: Establish AI ethics boards to oversee algorithm design and deployment, ensuring adherence to fairness, accountability, and transparency principles.
Emerging Technologies and Trends
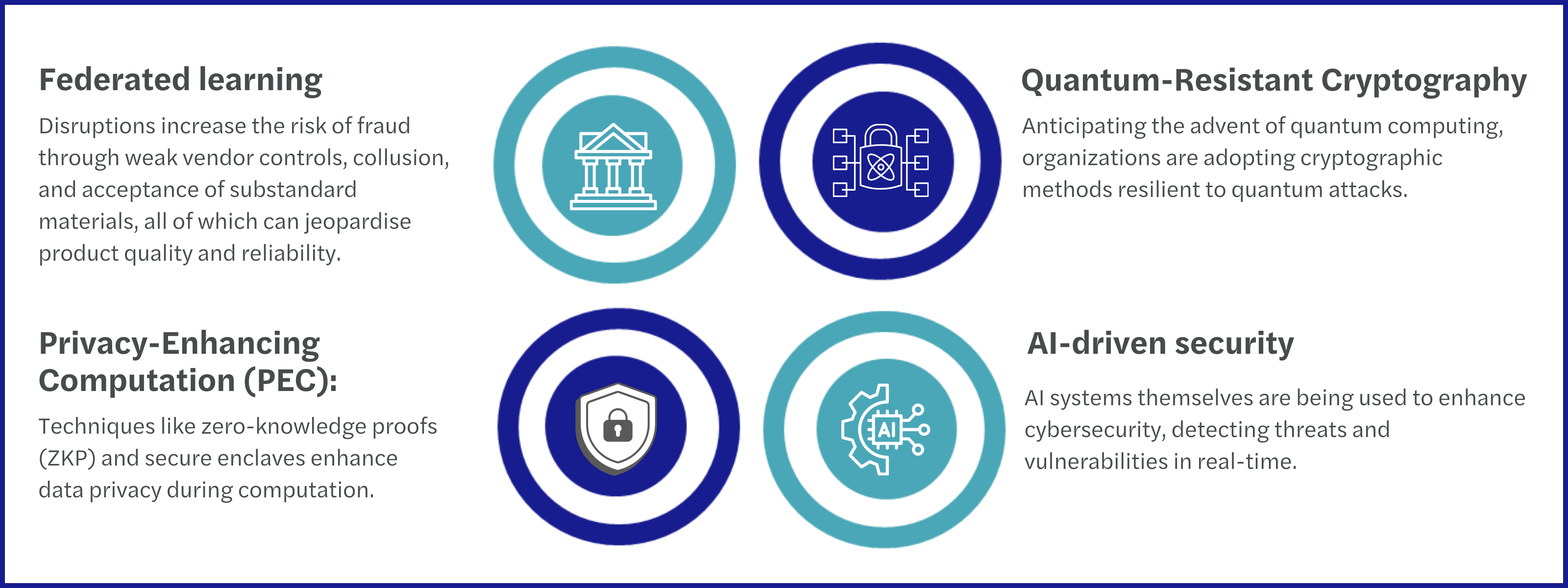
There are innovative technologies that are arising to address challenges of securing data in the algorithm age:
Case Studies
1.Financial services: A leading bank implemented federated learning to train fraud detection algorithms without sharing sensitive customer data. This approach improved fraud detection accuracy while maintaining privacy compliance.
2.Healthcare: A global pharmaceutical company utilized differential privacy techniques to analyze patient data for drug discovery, ensuring regulatory compliance and protecting individual identities.
3.Retail: A major e-commerce platform employed adversarial training to secure its recommendation algorithms, enhancing resilience against manipulation.
The problem of securing data in the age of algorithms requires the combination of technological innovation, regulatory adherence, and ethical stewardship. The key to ensuring trust and sustainable growth, therefore, is data security, which must remain a top priority for organizations using algorithms. Businesses can help navigate complexity in the algorithmic age by adopting the best practices. They can leapfrog emerging technology and build a culture of accountability regarding data.
Want to know more?